ITIL 4 Incident Management. Vendors sell SIEM as software as appliances or as managed services.

Itil Incident Management An Introduction Bmc Software Blogs

Incident Response Log Template Frsecure
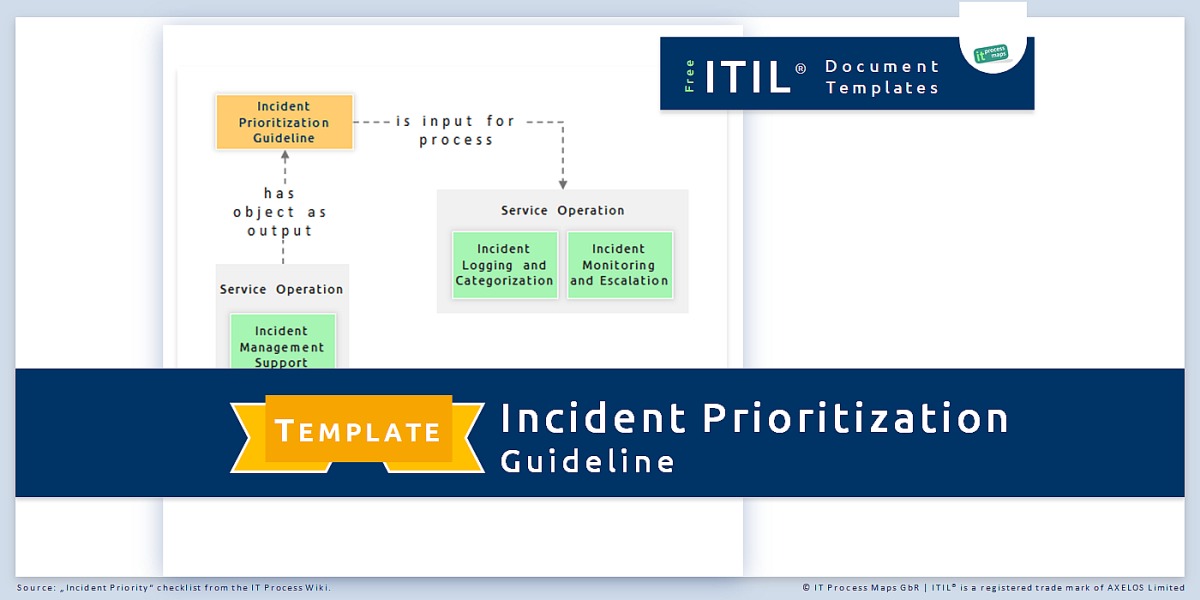
Checklist Incident Priority It Process Wiki
Incident History Powered by Atlassian Statuspage.

An incident logging system. An effective audit logging program can be the difference between a low impact security incident which is detected before covered data is stolen or a severe data breach where attackers download large volume of covered data. OnPage is a SaaS-based incident alert management system that can be easily integrated into incident management tools and hosted in secure SSAE-16 compliant hosting facilities across the US. Proper organization allows service staff can make more informed service decisions quickly identifying whether an incident is a known and easily.
Contact person name and phone number. Tier 1 covers the mandatory minimum package that all personnel being deployed on a WHO health emergency response must complete. Facilities Information Management System TRIRIGA.
It includes four animated online modules covering an introduction to emergency management WHOs role in emergencies the emergency response framework and the incident management system. A security incident is an event that may indicate that an organizations systems or data have been compromised or that measures put in place to protect them have failed. The Middle Fork Complex is being managed by a local Type 3 Incident Management Team.
Modern infrastructure has the capability to generate thousands of log events per minute. What is a security incident. Squadcast paves the way for a better incident management approach that addresses product concerns by facilitating a safe delivery method while providing a high level of system reliability.
ITIL V4 is no longer prescriptive about processes but shifts the focus on 34 practices giving organizations more freedom to define tailor-made processes. Continue to reduce logging debris and stabilize fire lines on steep slopes to reduce erosion potential. Incident Identification Logging and Categorization.
They provide real-time analysis of security alerts generated by applications and network hardware. Complete an incident intake report which should include the following information. The Incident Management process described here follows the specifications of ITIL V3 where Incident Management is a process in the service lifecycle stage of Service Operation.
Incident title along with type and brief description. Once identified as an incident the service desk logs the incident as a ticket. Incident reporting must go through the Service Desk providing Users with a single point of contact All incidents must be logged prioritized and solutions recorded in the Incident Management System One standard Incident Management Process is defined and used to support all IT Service users.
System hardware inventory as required by the Annual Registration control Logging information as required by the Audit Logging control Procedures for reporting and handling a suspected incident including. But will not be prompted to change their password immediately on logging in. In this situation you need to choose which logs to send to a log management solution and which logs to archive.
Get current service status recent and historical incidents and other critical trust information on the Okta service. WITS Login Page Use only after you have obtained a user account for WITS New WITS users. Resources are also positioned to respond to debris.
Please be sure you are using the right system to submit your report. UC San Diego 9500 Gilman Dr. Without appropriate audit logging.
All vacuation levels have been dropped in the Oakridge and Westfir area by Lane CountyFor current evacuation information and an interactive map of evacuation areas visit. Getting started with WITS There are two steps to obtain a user account for WITS. It is also assumed that the reader has a working knowledge of the NICS feature set such as logging in joining an incident opening Incidents and Rooms viewing data GIS AVL Weather etc reviewing completed documents.
Frequent monitoring and logging components are required to effectively assess information system controls operations and general security. Incident Identification and Logging. In IT an event is anything that has significance for system hardware or software and an incident is an event that disrupts normal operations.
Effective incident categorization streamlines incident logging reduces redundancy and speeds up the resolution process. Incident Identification is either done via testing using tools or otherwise user feedback infrastructure monitoring etc. Within priority 1 areas crews and equipment will continue to remove the hazards along public rights of way.
The IT team needs to capture complete information about the incident using a form template to speed up recovery process. SRE in product management is a data-driven approach for prioritizing the reliability of your most crucial features. Security information and event management SIEM is a field within the field of computer security where software products and services combine security information management SIM and security event management SEM.
La Jolla CA 92093 858 534-2230. Logging an incident simply means recording the following info. The ticket should include information such as the users name and contact information the incident description and the date and time of the incident report for SLA adherence.
As well as the National Incident Management System NIMS. You can email webappsloginassistancedesemogov or call 573-522-3207 if you need assistance logging into DESE Web Applications. Does this situation have anything to do with the Public School Retirement System PSRS Public Education Employee Retirement System PEERS data.
Logging the important parts of your systems operations is crucial for maintaining infrastructure health. Use your CARES user ID to apply for a WITS account. All events need to be documented within 24 hours of the occurrence.
The first step in Incident management is to report the identified incidentThis can be done by the end users themselves or agents can do it on their behalf. This policy provides a set of logging policies and procedures aimed to establish baseline components across the LEP. Obtain state DOA security clearance through the WAMS website.
With the Incident Command System ICS 3. If youve lost your password or experiencing problems logging in please contact the Administrator at. If you are already registered to use the CARES WorkerWeb you already have clearance.
ExactAppropriate date and time of occurrence. When a work-related incident injury or illness occurs or you witnessare involved in a near-miss incident please document the event by logging into the system using the link below.
Service 2 Principles Incident Log

Incident Report Template Major Incident Management Incident Report I Itil Docs Itil Templates And Training Courses
Incident Logging And Categorization Process So 2 1
How To Test Centralised Logging

How To Write An Incident Report Templates Venngage

10 Best Incident Management Software 2021 Rankings
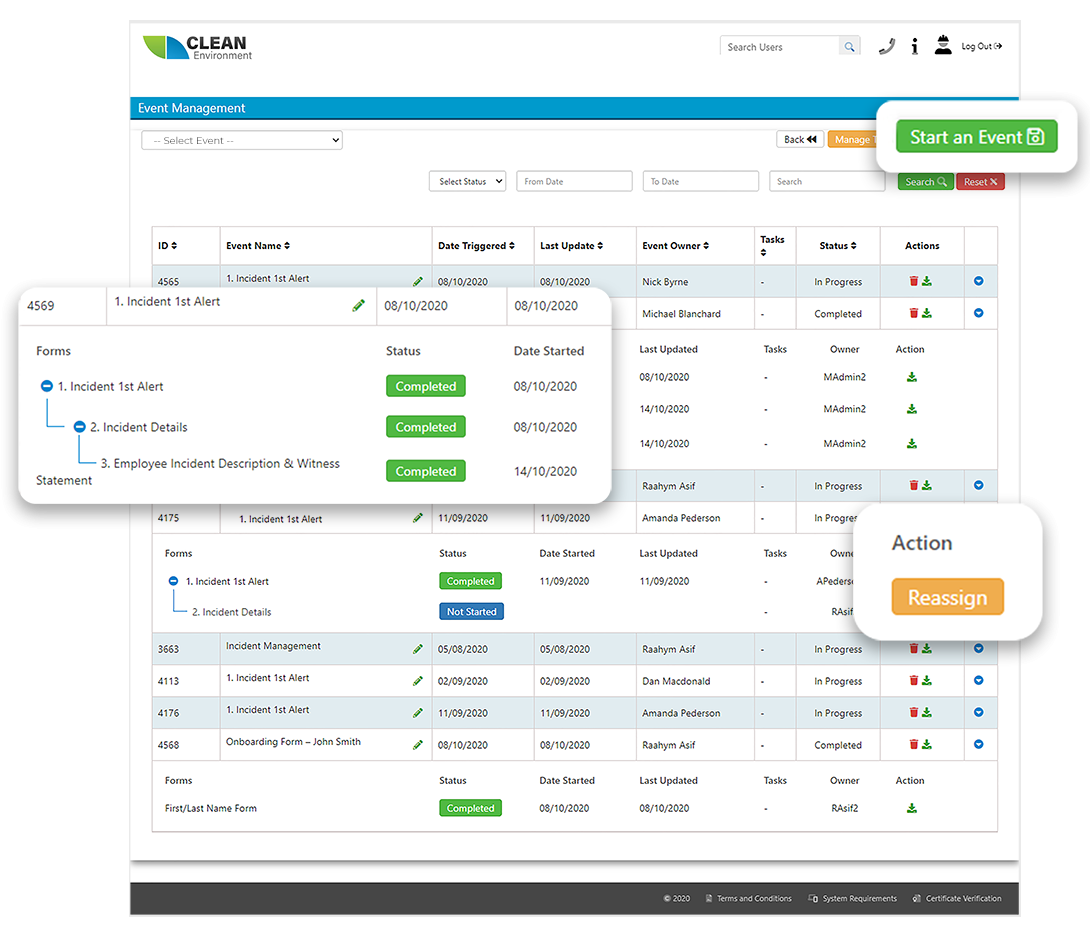
Online Incident Management Incident Reporting Software

Incident Management It Process Wiki

